In a previous blog, we discussed internal risk control assessment and introduced a comprehensive risk assessment tool, the Risk Control Matrices (RCM). This blog will address the risk assessment scales and options to respond to risks.
Blog
How To Avoid Sarbanes Oxley Pain
Your “how to” blog post should teach the reader how to do something by breaking it down into a series of steps.
Begin your blog post by explaining what problem you are going to solve through your explanation and be sure to include any relevant keywords. Add in a personal story to establish your credibility on this topic. And make sure to end your blog post with a summary of what your reader will gain by following your lead.
Internal Controls Boot Camp
Internal Control Risk Assessment

We have discussed the Control Environment in a previous blog. This blog will address Risk Assessment.
Businesses face a wide range of risks, including industry risk, strategic risk, operation risk, compliance risk and financial risk. Some risks are relatively significant, which may cause loss of profits or even bankruptcy. A classic example of industry risk is when film giant Kodak filed for bankruptcy after consumers embraced the newer technology of digital cameras and the film era ended.
What Is Internal Control Environment?

Before discussing internal control environment let’s briefly review the definition of internal control.
COSO (The Committee of Sponsoring Organizations of the Treadway Commission) defines internal control as a process, effected by an entity’s board of directors, management and other personnel, designed to provide reasonable assurance regarding the achievement of objectives.
Fraud Risk in Internal Control System

Internal control risks in business include the lack of sound internal control environment, poorly designed business processes, IT security risk, integrity and ethic risk, human errors and fraud risk.
The ACFE (Association of Certified Fraud Examiners) uses the fraud triangle as a model for explaining the factors that cause someone to commit occupational fraud.
8 Keys To Effective IT Change Management
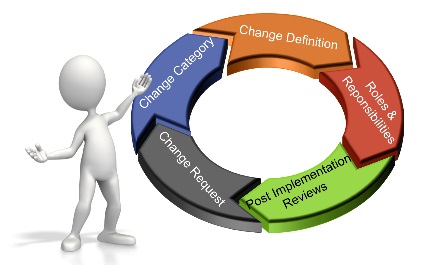
Effective management of change provides a structured, consistent, and measurable change environment to be utilized across an organization and is a critical component in the success of its daily business. Its goal is to increase awareness and understanding of proposed changes across the organization and ensure that all changes are made in a thoughtful way that minimizes negative impacts to services and customers. An organization should have a document that defines the implementation of Change Management procedure. The computing systems, networks, peripherals, and associated facilities are subject to continuous changes driven by new technology, evolving business requirements, changing contractual requirements, and growing regulatory policies. Effective change management applies to both systems and supporting infrastructure, and is a necessary component for the continuous success and growth of the organization.
Effective Change Management – Change Communication

Effective management of change provides a structured, consistent, and measurable change environment to be utilized across an organization and is a critical component in the success of its daily business. Its goal is to increase awareness and understanding of proposed changes across the organization and ensure that all changes are made in a thoughtful way that minimize negative impact to services and customers. An organization should have a document that defines the implementation of Change Management procedure. The computing systems, networks, peripherals, and associated facilities are subject to continuous changes driven by new technology, evolving business requirements, changing contractual requirements, and growing regulatory policies. Effective change management applies to both systems and supporting infrastructure, and is a necessary component for the continuous success and growth of the organization.
How to Prevent Security Incidents

No industry or organization is immune to cyber security attacks or a data breach. Network security threats exist perpetually and eliminating all computer security risks may be an impossible task. However, there are recommended measures and best practices which can increase the effort required to breach a network or to compromise data security. Effective security practices should be incorporated into the overall security defense strategy to protect an organizations’ network and resources. Preventing problems is far less costly and more effective than reacting to security incidents after they have occurred.
Effective Change Management – Documenting Changes

Effective management of change provides a structured, consistent, and measurable change environment to be utilized across an organization and is a critical component in the success of its daily business. Its goal is to increase awareness and understanding of proposed changes across the organization and ensure that all changes are made in a thoughtful way that minimize negative impact to services and customers. An organization should have a document that defines the implementation of Change Management procedure.


